Introduction
Modern team sites are perfect for fast collaboration, but many enterprise companies requires a managed approach. I often experience questions like:
- How do we get an overview of all users and their permissions in a single view?
- Can we use Active Directory groups?
- Can we prevent users from sharing content with others?
- Can we prevent breaking inheritance of permissions?
- What about old SharePoint groups can we use them?
During this article I will try to answer the questions above and give an overview of permissions for a modern team site.
Creating a modern team site
Lets start by creating a modern team site.
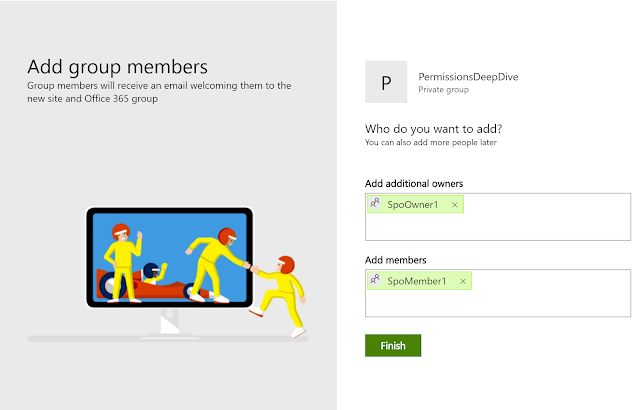
Log into your tenant and create a new team site:
Notice the last image. You can add members and owners only.
Site Permissions
In the previous section we added SpoOwner1 as owner, and SpoMember1 as member to the site. Lets see what happened, but before that lets have a look back to the old classic SharePoint days.
Classic SharePoint Site
Below we see a classic site settings page:
We have a Permissions section where have a very fine grained control of SharePoint groups. Lets have a look at Site permissions:
Here we can see the different groups on the site, and notice each group has a permission level we can configure dependent on our requirements. Try to click on Permission levels in the top:
Here we see the default permission levels, one for each group. Lets have a look on a permission level:
Above is only a subset of all the permissions you can set. Lets make a last test too. Go back to a SharePoint group and lets add an Azure Active Directory:
As you can see, I can add an Azure Active Directory group to a SharePoint group. Very often sites are managed by adding one or more departments etc to SharePoint sites to obtain some kind of governance level.
If we summarize on the classic section above, we have a very fine grained control over permissions. If we have a requirement that we want to add an department to x numbers of sites we can do it by adding Active Directory Groups to the SharePoint groups.
Modern Team Site
Lets try to do the same exercise again, but for a modern team site. Below the site settings for a modern team site is shown:
As you can see above the permissions section is gone. Lets cheat a little and go to the classic permission settings page /_layouts/15/user.aspx (add this to the url):
Here we can see there is three SharePoint groups. In the Members group there is a group (we will get back to that) called PermissionsDeepDive Members, and the two other groups are empty. When we created the site we could add Owners and Members, so where is the Owners? To answer that question I have to cheat a little again. This time I navigate to following url for the site /_layouts/15/mngsiteadmin.aspx to see Site Collection Administrators:
Once again we have a group that is added to SharePoint, and that group is site collection administrator on the site.
But where do these two groups come from?
Office 365 Groups
I wont go deep into what a Office 365 group is. There is plenty of articles on that. One of my personal favorites can be read here: office-365-groups-explained. In short an Office 365 is a central place to store member ship for multiple products. It was not very clear, but when I created a Modern Team Site I actually created an Office 365 group with following Components:
- Office 365 security group
- SharePoint Online Site
- Shared Outlook Calendar
- Shared Mailbox
So we got much more than just a SharePoint site. If I go into my mailbox, and look under Groups section I can see my group:
In the top you can see I have a mailbox, Files (SharePoint), Notebook (OneNote), Planner ..
This is why we can't have all the fine grained SharePoint permissions anymore. We need a more simple model that can be managed across multiple services in a central place.
Site Permissions
OK, that is all good. Microsoft has hidden all of the technical stuff for a reason, so where do we see site permissions on a modern team site? Lets get back to the modern team site front page and click on the members button in the top left corner:
Clicking that gives the following view:
It is important to highlight here, that what you see is taken from the Office 365 Group and not the local SharePoint Group. If you cheat a little and add other users to the local groups, they are not viewed here. Another very important thing here is you cannot add groups to an Office 365 Group. Do you have a scenario where you need to add an organizational unit to a large amount of sites, and manage them through Active Directory group you need develop a customized solution or find a partner product.
You can only have owners and members. Only owners can grant permissions on the site level, however members can grant permissions on list level (we will get back to that next).
So what is my personal thought on this? As the article is written I am working for Microsoft, but this article is my personal point of view and observations. I have kind of mixed feelings here. There is so many new cool features in the modern look and feel, and having shared calendar and mailbox is really cool. On the other hand in many enterprise scenarios the lack of Active Directory Groups is a big problem, that in many scenario's requires a custom solution.
Folder and File Permissions
If you think I am finished and there is no more important permissions settings left to discuss, your very wrong. But this super exiting subject should keep you going - your already this far so why not 😂
Lets look at permissions on files and folders level. On the image below you can see the permission settings for a folder:
Notice we have a new permission level to the left (Visitors). What we see here is not the Office 365 group anymore but the local SharePoint groups. In the top you can grant access to specific users, and if you add a new user with read permissions, its not added to the local visitor SharePoint group but in the root with read permission level. So I am not sure why the Visitor group is even there.
Another very important observation is that you can actually add Active Directory Groups on files and folders.
If you add a user that is not added to the site to a specific file or folder (break permissions), then the user needs to link directly into that file or folder. Accessing the site will give a permission error.
Getting a permission view
Very often enterprises has a requirement to get an overview of who has access to what. As you seen earlier in this blog, on site level that is easy. But if you need it on broken permissions, on files and folders it is another story. For most levels in Advanced Permissions there is a check permission for a specific user. However it wont give you a usable view. There is different partner solutions on the market, else you have to create a custom solution. The PnP framework has features that can provide you that kind of information, see Meassure-PnPList. If you have very large lists, notice getting this kind of information can run for days. So plan for some kind of compute strategy with Azure functions etc.
Conclusion
My take ways from the post is:
- Site permissions are controlled using Office 365 Groups where content are controlled via classic SharePoint groups
- You cannot add AD groups to Office 365 Groups and by that site permissions (you can use dynamic groups to some extend)
- You can add AD groups to content in lists and libraries
- If you only add users to a give folder or file, they need the direct link to that file or folder. They cannot access the site url
- There is no complete permissions overview
Is Modern Team sites then the way to go? I would say so. There is no doubts, that this is the template Microsoft is betting on. Going forward this will get better and better. Just the look and feel is enough seen from my point of view. That said I hope we will see better management tools going forward.